If you see a single Bluehost hacked website, eventually, all your websites on the same panel will be hacked. If you have a server or shared hosting, you will see the attacks on all your websites.
There are two main reasons for this. It’s either your hosting provider’s security breach (which has less than a 5% chance) or the other 95% is where the vulnerability has come from your end.
In the past, we have cleaned multiple websites of our clients facing the same issue. Having cleaned these many websites, we have an exact step-by-step guide to restore your website.
We will check out automated ways and manual ways to clean it. Lastly, we will tell you how you can secure your website.
If you see a Bluehost account suspension notification, we will tell you how you can fix that too.
Let’s dive in.
Why was the Bluehost website hacked?
It might seem boring but it’s important to know why the Bluehost website was hacked in the first place.
The common cause for Bluehost site hacking is WordPress plugin issues. As WordPress is a popular CMS, there are many outdated plugins, which attract hackers to compromise all the websites at once.
Below are a few types of plugins that are usually vulnerable.
- Outdated plugins.
- Plugins installed from an untrusted source.
- Nulled/cracked plugins.
- Custom plugins.
Plus, if your site is hacked due to above reasons, changing the host won’t help either, as the issue lies in the site.
How can Bluehost Hacked Website and Account Suspension issues be fixed?
We will now list down a step-by-step guide to fix Bluehost’s hacked site and recover Bluehost’s suspended account.
Step 1 – Identify the problem
The first step is to identify the problem. Don’t waste more time and directly head over to Bluehost customer support.
- Ask them to reactivate your account in case it is suspended.
- Request a complete scan of your cPanel.
- Don’t buy a SiteLock license even if they ask you to.
- You can use Sitelock lite (free version) to perform a full scan on your website.
Step 2 – Manually clean
Manual cleaning looks like a tedious job. But, it’s the BEST way to fix Bluehost’s hacked website in no time.
The first step here is backup. Make sure you have a backup of your existing site (if you don’t have one, you can take a backup of your current hacked site).
Start by deleting all the unused plugins and update the rest of them. Do the same thing with themes. If you are using nulled/cracked plugins, you can delete them.
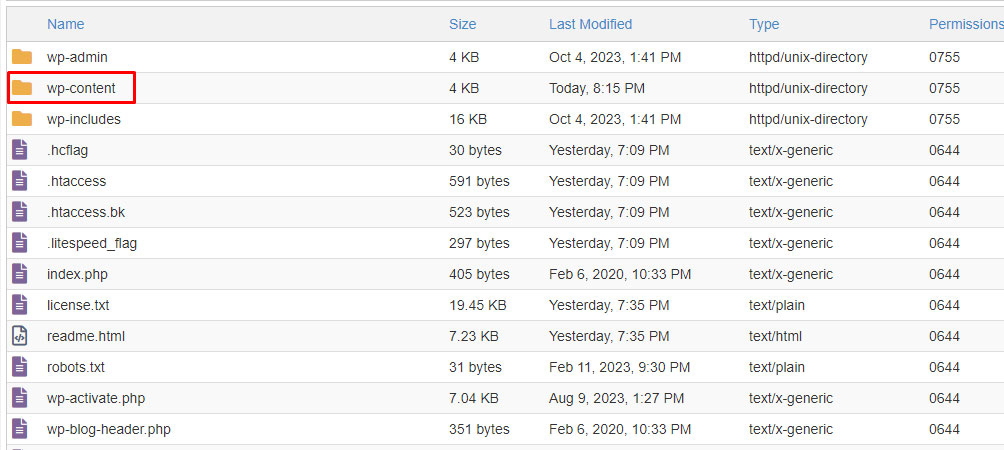
You can do it by heading over to wp-content and looking for themes and plugins folders.
We will now replace core files. Here are steps to follow after that.
- Download WordPress from the official website.
- Upload the zip on the main directory where you have your current installation (assume it’s on public_html.
- Create a new folder (let’s name it New) and extract the WordPress there.
- Delete the wp-content folder and wp-config.php files from the new WordPress.
- Now, head over to the existing directory (public_html) and delete all the folders and files from there except the new folder that we created, wp-content folder and wp-config.php files.
- Move the folders/files from the new WordPress to the current installation (public_html).
- That’s it, do the same steps for all the websites.
Don’t just replace your files, instead, you will have to delete the existing files and then move the new ones. Sometimes, a Bluehost’s website that is hacked will have new virus files created.
Replacing the core files won’t delete such files.
If for some reason, you can’t access your website properly, you can log in as an admin, head over to settings > permalinks, and hit the save button.
It will regenerate the .htaccess file and you will see your website working again.
Now, look for other backdoors. Check for the following keywords inside your files. You can see it in the wp-content and wp-config.php files as we have replaced other files.
Look for the following keywords in the files with PHP extensions.
- eval
- base64_decode
- gzinflate
- preg_replace
- str_rot13
You can also see if the files have any suspicious code in them. Wondering what’s suspicious? It’s usually encrypted and doesn’t look like normal code. You will see a huge jargon of numbers and letters.
Refer to the below image to know what the malicious code in the Bluehost WordPress website looks like.
As you can see the malicious code is utilizing base64_decode, str_rot13, preg_replace and eval. This is what encrypted code looks like. In almost all cases, this code is malicious and creates a backdoor on your website.
So, it’s always better to delete them.
Step 3 – Install Security plugins for malware removal
We will take it to a new level now by adding the security plugins on your WordPress website.
Wordfence
Wordfence is the best security plugin you can consider. Don’t worry, they also have a free license. For most websites, their free license is enough.
You can opt for their pro version if you have a bigger website.
Just head over to the “scan” option from the Wordfence menu and start a full scan.
It might use your server resources to do some scans. Therefore, don’t worry if the website doesn’t load during this scan. It won’t take much time.
Once the scan is completed, you will see the options to repair them. However, we would recommend replacing the entire file with the new file.
You can get the new file from the WordPress core zip or you can look for the directory path to know the file type.
If the files are NOT from the core files, it’s recommended to delete them.
Anti-Malware security (for scanning)
You can then try using Anti-malware security for further scanning. It sometimes detects malware that Wordfence can’t. So, just to be a bit more safe, you should try it too.
However, you should not use both plugins together at the same time as it can cause conflicts. So, make sure that you deactivate the first plugin before you activate another.
By now, you have pretty much cleaned the entire website. Your website will work normally. You can still follow the below steps if needed.
We would recommend you ask the support to rescan the website and see if there are more malware-affected files. Make sure you take a clean backup of your fixed Bluehost compromised website.
Step 4 – Restore older version
Don’t try this before trying the above ones. It’s the last option.
If you use the Softaculous installer, you will have a backup. You can try restoring an older version. For future backups, you can use one of the backup plugins instead of using Bluehost backups.
Step 5 – Hire a Developer
You can always hire a developer or a security professional. They will save you time as they might have already come across similar issues.
Step 6 – Rebuild you site (optional)
Wait for a few days after trying all the things above, if your site gets infected again and it becomes a recurring issue, here’s the ultimate fix for the hacked Bluehost website.
There are two ways to rebuild your Bluehost hacked website, you can either completely start with a fresh installation and import the database or you can keep the DB as it is.
For most hacked Bluehost sites, databases aren’t affected. So, you just need to replace all your files.
Here’s a way to do it.
- Delete all folders except wp-content.
- Now, enter inside wp-content and delete all the folders/files except “upload”. This is where your images are stored.
- Open your upload folder and delete all the files that end with “.php” extension.
- That’s it, now you can move the upload folder to somewhere safe.
- Download WordPress from the official website and extract the content there.
- Go to your saved upload folder and move all the files to wp-content > upload.
- Now, you can go back to the main directory and look for the wp-config file.
- Open the file with the code editor and enter necessary details like database name, username for cPanel, database username, password, etc.
- If you can’t find any of the above information, simply contact Bluehost support for help. They will guide you through the process.
- Open your WordPress.
- If you see any issues, you can log in via admin and go to settings > permalinks, and then hit the save button without making any changes. It will regenerate your .htaccess file.
- Now, you can use a wp-optimize plugin to clean and optimize your database.
How to prevent being hacked again?
If you have contacted Bluehost, you would know that it’s not good enough to rely on them. Rather, you need to secure your site yourself. Here are some ways to do it.
1. Upgrade to VPS or Dedicated
Having a VPS means you get more permissions as compared to a shared hosting. You can easily have more than 1 cPanel or you can isolate each website.
In this way, if your one site is hacked, others will be safe as they are kept and served separately.
Alternatively, you can have different hosting accounts for different websites on shared hosting which could cost you more.
2. Fix Server Misconfigurations
- Weak file permissions: Make sure you have proper file permissions. If hackers can access one of your Bluehost files i.e. configuration files containing credentials or other sensitive information, they can hack your entire panel.
- Open ports: If you use Bluehost VPS, make sure you have no open ports.
- Enable two-factor authentication: Bluehost cPanel allows 2-factor authentication. You can enable that.
- Remove old files: Make sure you remove license files, readme files, and other software junk files after installation.
3. Keep everything updated
Enable auto-updates. If not, make sure you have updated WordPress, themes, and plugins.
Use a child theme instead of the main theme. Lastly, make sure you have installed the themes and plugins from trusted sources or the marketplace.
4. Optimize security plugin
Usually, the security plugins are optimized. It’s still recommended to ensure the configuration of your security plugin.
Wordfence has a lot of tutorials on how to harden the plugin. For instance, you can make changes to the brute force protection option. The below image refers to the default option.
You can decrease the number of attempts before the user gets locked out.
Some of these options are applicable to all users and not just admins. So, keep that in mind while you are configuring. It’s always recommended to check out documentation if you want to make some advanced changes.
5. Check anonymous accounts
The biggest issue you will face is spam accounts which might hack your website. So, regularly check for new users on your website.
You should also ensure that you are not using the default username (admin or your domain name).
6. Migrate to a different host
Bluehost shared hosting had many big issues in the past and Bluehost is still not doing enough for the security of their users. The Sitelock premium is expensive and is of no use.
Previously, they had a good reputation. However, in recent years, it’s getting worse.
The best thing is to migrate from Bluehost to another secure host.
What to look for in the new host?
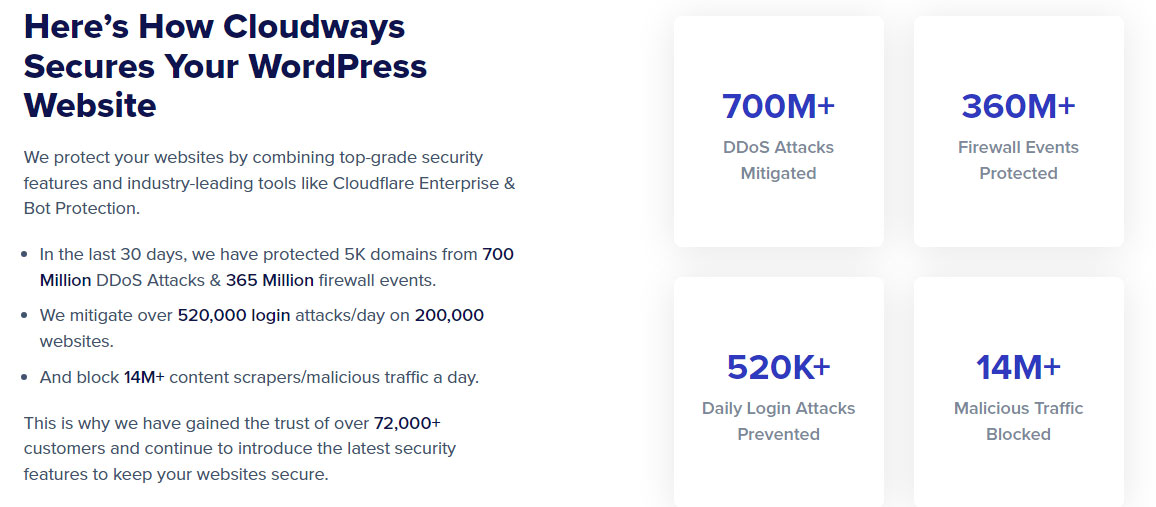
The new host should have a decent security platform such as Imunify to protect you from malware. Cloudways hosting is the best when it comes to cloud security.
They provide an extra layer of security to the existing data center.
You can choose Digital Ocean as your data center inside Cloudways. With this, you can have a fully secure cloud server with an excellent user-friendly panel at the cost of shared hosting.
Cloudways is easily scalable too. Above all, it’s super-secure.
Other VPS usually cost a lot. So, if you want cheaper alternatives, you can also go with unmanaged VPS. However, it requires a decent amount of technical knowledge.
So, we would recommend going with Cloudways.
For instance, if there is an attack on the Bluehost server, they will first fix their shared hosting server farm (server cluster) rather than fixing all the VPS servers.
The same goes for other hosts.
Is Bluehost Sitelock worth buying?
No, Bluehost Sitelock is not worth buying. The addon does almost nothing. The same features are provided by many good WordPress plugins. You can use any of them for security.
WordPress is huge and an easy yet large target for attackers. On the plus side, it’s easier to fix hacked WordPress on Bluehost.
Reviews of Bluehost customers
Bluehost is good only till you don’t face any issues. Once you start facing issues, it’s worse.
Here’s a customer review where they even paid for Sitelock and Bluehost was trying to sell them more security add-ons.
Sometimes, the addon isn’t even implemented.
The same thing has been going on for years now. Here’s a bit older review saying it takes a lot of time to do the scan.
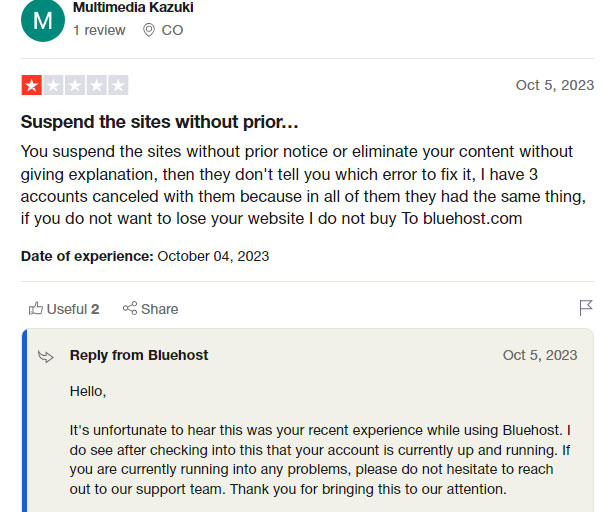
The same suspension issue exists. Here’s a recent review. Bluehost suspends the account without warning. Even if you contact the support, the account might still get suspended.
Conclusion
It doesn’t matter if you set up a fresh installation of WordPress, if you don’t take proper steps to secure it, your website will eventually get compromised.
There are fewer companies that invest in commercial software for security. Instead, they use freeware scanners for security. For this reason, it lacks the overall security on your hosting.
A good option for secure WordPress hosting is Cloudways. It comes with:
- Dedicated firewall and Malware bot protection.
- DDoS protection.
- Application isolation, and much more.
You can also try out Cloudways for free. They offer a 3-day trial.
FAQ (Frequently Asked Questions)
How secure is Bluehost?
Bluehost provides basic security features. However, it’s not secure enough for all the websites.
Can a Bluehost account be hacked?
Yes, any hosting account can be hacked including Bluehost if you don’t take proper precautions.
Does Bluehost protect against DDoS?
Yes, Bluehost can protect against mild DDoS attacks.
How do I fix Bluehost malware?
Setting up a fresh installation and importing the existing database is the best way to clean the malware. It’s recommended to follow the full step-by-step guide to avoid any damage to your site.










Web Hosting Expert, Content Writer, SEO Consultant, and Web Developer with over 10 Years of Experience.
He has a passion for technology and has spent over a decade reviewing and testing web hosting companies to provide his readers with honest and accurate reviews of the companies he had experiences with.
Tommy loves helping people and has helped hundreds of people start their own successful blogs.